Setting Up Comet Connect.
From CometWiki
Setting Up Comet Connect
There are 2 main steps to setting up a new CometConnect account:
- Define the privileges of the account
- Define the privileges of each user in the account
Defining the Account
To create the new account, we’ll need the following information:
A name for the account. This name will be used as part of the identifier at the top of each user’s screen. A couple of examples are the name of the company such as “ABC Plumbing”, or the purpose of the account such as “My Demo App”. The account name is limited to 30 characters.
A list of Comet directories for the account’s application. By default, each account will be given their own REL, UTL, COS, and TMP. If the XAP option is purchased, they will also have an XAP directory. In addition, you may name other directories you’d like to have for the account’s programs and data files. They may be called anything you like. A total of 10 directories is allowed for an account. Individual user’s access to the directories may be controlled thru the use of the QMONITOR password scheme.
The total number of sessions purchased for the account. As you will see below, these sessions may be divided up in any manner between the individual users in the account.
Defining each User
For each user we’ll need the following information:
A descriptive name for the user. This name will be used as part of the identifier at the top of the user’s screen. It may be their real name such as “Jim Guerber”, or it may be a description such as “Inventory Reports”. The user’s name is limited to 30 characters.
A login name and password for the user. By default Comet Connect users will be asked to identify themselves with a login name and password. The login name is limited to 12 characters and is case-insensitive. The password is limited to 32 and is case-sensitive. If you wish, we can identify the user by their unique Comet Anywhere ID (CAID), so the username and password will be used only for the first time that user logs in. If you desire even greater security, you may request that we check both their username/password and their CAID.
The name of the program to run at login. By default, the standard QMONITOR will be run. If you prefer to skip QMONITOR and go directly to a menu or other program that is the name we’re looking for here. (If you wish to setup QMONITOR security using the blind password, you may do so yourself once the account is up and running.)
Whether or not this user should receive a copy of the daily backup of the account’s files. Each night a backup of all the account’s directories is taken and packaged into a .zip file. You may designate any or all of the users in the account to receive this .zip file the first time they login the following day. The .zip file is transferred using CopyFile. See below for more on backup.
Whether or not this user should receive automatic Comet updates. The Comet Connect machine will always be running the latest stable version of Comet. We recommend that the remote users remain up to date by receiving the automatic updates, but if you prefer you may request not to be updated. In this case, it will be your responsibility to update the remotes manually.
The number of sessions allowed for this user. You may designate any number of the total sessions available to the account for each user. Comet Connect keeps track of the number of sessions in use at any given time for each user as well as each account. Therefore, regardless of how many sessions you allow for a user, the total number of sessions in use by all the users at any given time will not be allowed to exceed the total for the account. For example, if the account purchases 5 sessions and has 3 users, you may allow each user to have a maximum of 3 sessions, but if one user has 3 then only 2 remain for the other 2 users of the group to share.
The TERM$ value for each session. This is optional. Some applications rely on TERM$ values to identify a user. For example, you may want Tom to always get terminals T00 and T01 and Steve to get terminals 215 and 216. If you do not specify the TERM$ value, it will be assigned by the system when the user logs in.
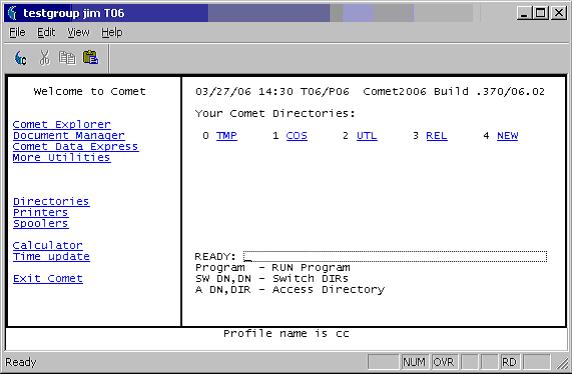
Once we have all the account and user information, we can quickly set up the service. Here’s a snapshot of a typical QMONITOR screen. Note the account name (testgroup), user name (Jim), and session number (T06) at the top of the screen:
Backup
We think your data is very important. Whether it is ever used or not, you will feel much more secure with the knowledge that your data files are stored on more than one computer. Every night at 1:00 Pacific Time, CometConnect starts a backup run foll accounts. You may specify what data is to be backed up down to the file level. CometConnect uses WinZip version 10.0 for the backup procedure and collects backup files for at least 30 days.
You may choose to encrypt the backup files with 128- or 256-bit key AES encryption by specifying an encryption key (the longer the better). The AES was announced by NIST as an approved encryption technique for use by the U.S. government, private businesses, and individuals. When properly implemented as a key component of an overall security protocol, the AES permits a very high degree of cryptographic security, yet is fast and efficient in operation. It is your responsibility to keep the encryption key secret. Once the key is given to us, we may not be able to reproduce it if it is lost.
You also should designate one or more users as backup recipients. The first time these users log on to CometConnect each day, the current backup file will be transferred to them. The backup files will be identified by the account name and date. Without the encryption key, if backup encryption is chosen, the backup recipients will not have access to the contents of the backup files even though the files are transferred to their computer. For extra security, you may designate multiple users as backup recipients. Each of those users will receive a copy of the current backup file when they log in.
Even though the files are compressed, you must designate the files that are to be backed up in such a way to strike a balance between the thoroughness of the backup and the inconvenience of the time it takes to download the backup file each day.
Copyright © 2006 - 2007 Signature Systems, Inc.